Key points:
- 50% of all Cyber Incidents for Mandatory Data Breach Notification are Phishing (Compromised Credentials)
- Business Email Compromise can lead to $120,000 lost
- 2 Factor Authentication for online services can protect you from compromised credentials
On Tuesday 30th October 2018 the Office of Australian Information Commissioner released the Quarterly Report for Notifiable Data Breaches from 1st July -30 September 2018. Some key statistics are:
- 57% (139) of Notifiable Data Breaches are Malicious or Criminal Attacks
- 69% (96) of Malicious or Criminal Attacks of Notifiable Data Breaches are Cyber Incidents
- 50% (48) of Cyber Incidents are Phishing (Compromised Credentials)
Phishing Campaigns
Examples of Phishing include Westpac Bank emails telling the customer that their credit card is temporarily locked and they need to go to an attacker controlled Phishing Website that looks like a Westpac Bank website to login to the netbank application with their credentials. These credentials are then used by the attacker to log into the netbank and transfer money out of the bank accont.
Phishing campaigns are used by criminals as they are extremely effective at collecting credentials as humans are the weakest link in the security chain and will click on unsafe links. If you can convince a target to click on a link and login somewhere that isn’t the correct site, and trick them into giving away their credentials then you can use the credentials to steal data.
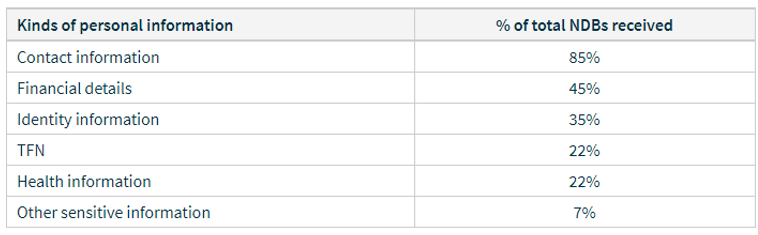
Data that was stolen as part of the Australian Notifiable Data Breaches is the following in July-September 2018:
Spear Phishing
More targeted examples of phishing include Spear Phishing and Whaling. Spear Phishing is where there is a particular person such as an executive that you are wishing to target. This may include research that has identified that they like golf and so the attacker sends an email to the executive’s email address with an advertisement for a free round of golf at a prestige golf course. The link that the executive clicks on to redeem the voucher takes them to an attacker hosted website which downloads malware to the executive’s computer. This could be achieved by using an exploit kit such as Angler Exploit Kit. The attacker then has compromised the target’s computer and can do anything they want with it.
Business Email Compromise
If an attacker has stolen credentials to an email system such as Office365 Outlook or Outlook Web Application then the attacker could intercept emails and impersonate someone. An example I have seen is that a law firm has been dealing with a client via email. Somehow the email of either the law firm or the client has been compromised and an attacker impersonated a lawyer from the law firm requesting payment to be made to the attacker’s bank account. The client did this and lost $120,000. All because they had either used a simple password that could be guessed, or used the same password as had been used at a website that had been breached, or had given their credentials to an attacker via phishing.
2 Factor Authentication
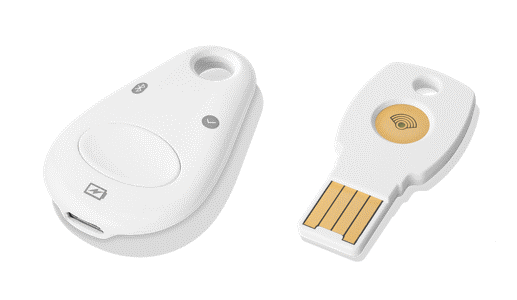
Google previously had a problem with phishing and having their employee’s credentials compromised. To combat this Google gave every one of its 88,000+ employees a hardware token that they can enter as part of a second factor of authentication. So every time a Google employee logged into their email system they would need to use this hardware token to be plugged into their laptop to provide another key to authenticate before being able to login. Almost overnight the Google phishing emails targeting Google employees were nullified as any credentials that may have been stolen would need to have the hardware key with them in order to provide a 2FA.
A hardware security key can be purchased from Yubico with their Series 5 keys or from Google with their Google Titan key.

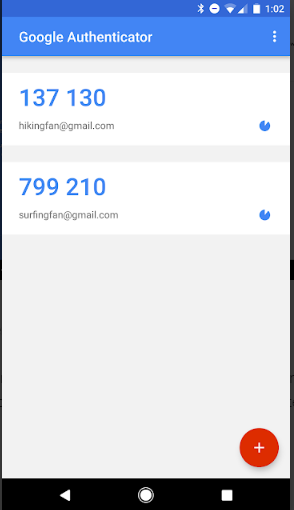
Another type of 2FA is the Timed One Time Passcode (TOTP) which is the code you will be sent via SMS or can be found using an Authenticator solution such as Google Authenticator or Authy. These are software based 2FA and can provide a similar layer of security as the hardware 2FA.
If you are being targeted by phishing emails then you should turn on 2FA for all of your online services that contain data that you log into. This 2FA can be a hardware key or a software key. As email is ubiquitous and may involve directions to transfer money it is recommended to turn 2FA on especially for email services such as Google G-Suite or Office 365 Outlook.